Attention, there is a new kind of virus spreading in the environment of 3Ds Max, which can not be detected by your antivirus software!
If your scene is infected or you want to avoid getting the virus into your 3Ds Max download and install share-ware script Prune Scene and activate the Active Protection!
After run Active Protection mode viruses will be deleted.
In the future, if the viruses get to you in the scene they will always be deleted!
Important!
You can use Prune Scene for free to clean up viruses!
Intro
Recently, there has been a high activity of infection of scenes and models with ALC BETACLEANER (Worm.3DsMax.ALC.clb) and CRP BSCRIPT (Worm.3DsMax.CRP.bscript) viruses at 3D stocks, online forums and online sharing services.
Typically, viruses get to you through an infected scene file (* .max) when you Open, Merge or X-Ref it.
When opening or working with an 3Ds Max software file (*.max), the scene displays some strange behaviours. Read about each virus in details below.
ALC BETACLEANER
This virus a 3rd-party Maxscript (hereafter called "ALC"), can accidentally corrupt 3Ds Max software's settings and be propagated to other Max files (*.max) on a Windows system if scene files containing the broken script are loaded into 3Ds Max. (The original script seems to have been included with some free 3Ds Max scenes that users may have downloaded from various online sources.)
Although the Maxscript appears to have been written as a form of copy protection for a commercial plug-in, if affected 3Ds Max scene files are distributed and re-opened, they may propagate the corruption problem to other copies of 3Ds Max.
This particular Maxscript file will be embedded into a Max scene file as a scripted controller.
The script saves itself into hidden files in the:
Files:
vrdematcleanbeta.mse
vrdematcleanbeta.msex
Note!
These files will have their System attribute properties set to Hidden, and are not normally visible in the Windows operating system's File Explorer. You may need to change the View → Folder Options to View Hidden Files and Folders.
This virus take next issues:
- Crashes or fails to open
- Corrupted scene data
- Empty helper nodes (¡¡×ý×û and ×þ×ü)
- Unable to save the scene manually
- Unable to use the Undo function (Ctrl+Z)
- Displays various Maxscript errors
- Corrupts or removes cameras, lights, and/or materials
- Forces an auto-save after breaking the scene or when choosing "Don't Save" when closing
- Adds itself to an existing script in the Maxscript startup directory
- Force closes 3Ds Max
- Unable to save V-Ray lights
CRP BSCRIPT & ADSL BSCRIPT
This virus a 3rd-party Maxscript (hereafter called "CRP"), can accidentally corrupt 3Ds Max software’s settings and be propagated to other Max files (*.max) on a Windows system if scene files containing the broken script are loaded into 3Ds Max. (The original script seems to have been included with some free 3Ds Max scenes that users may have downloaded from various online sources.)
This virus also distributed as ALC BETACLEANER when you open the scene. Virus spoils all scripts that are in your Maxscript startup folder, adding malicious code to them.
This virus take next issues:
This virus take next issues:
- Undo function (Ctrl+Z) is broken and no longer works after switching to different viewports
- Scene lights may disappear or be deleted
- Scene materials may deleted
- Damage scripts in Maxscript startup folder
- Scene objects may deleted
ALC2 ALPHA
The same as ALC BETACLEANER, but creates different malicious files and global variables in 3Ds Max environment.
The script saves itself into hidden files in the:
Files:
vrdematcleanalpha.mse
vrdematcleanalpha.msex
vrdestermatconvertor.ms
vrdestermatconverter.msex
vrdestermatconvertar.ms
vrayimportinfo.mse
Otherwise, the behavior is the same as for ALC BETACLEANER.
ALC3 ALPHA
The same as ALC BETACLEANER, but with some differences.
The most dangerous thing is that this virus can download updates for itself and can be modified!
This virus take next issues:
- Crash 3Ds Max when open
- Empty helper nodes
- Unable to use the Undo function (Ctrl+Z)
- Displays various Maxscript errors
- Change render settings (V-Ray): VFB size, materials, GI settings etc.
- Tiny save your render from VFB and send to remote e-mail
- Gather system information and send to remote e-mail: IP, MAC, HDD info, Memory, CPU, 3Ds Max version etc.
- Send gathered data from fake e-mail sss777_2000@126.com (nfkxovtedspjgedv) to rrr888_3000@126.com
- Download from remote address and update itself from http://www.Maxscript.cc/update/upscript.mse
Files:
vrdematpropalpha.mse
vrdematpropalpha.msex
DESIRE FX CA
This virus take next issues:
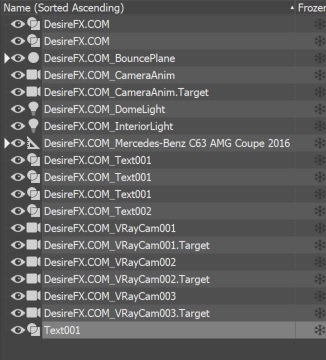
- Rename all objects in scene and adds advertisement prefix in name
- Create Text objects in scene with advertisement text
- Can write advertisement text in File Info
- Can freeze viewport
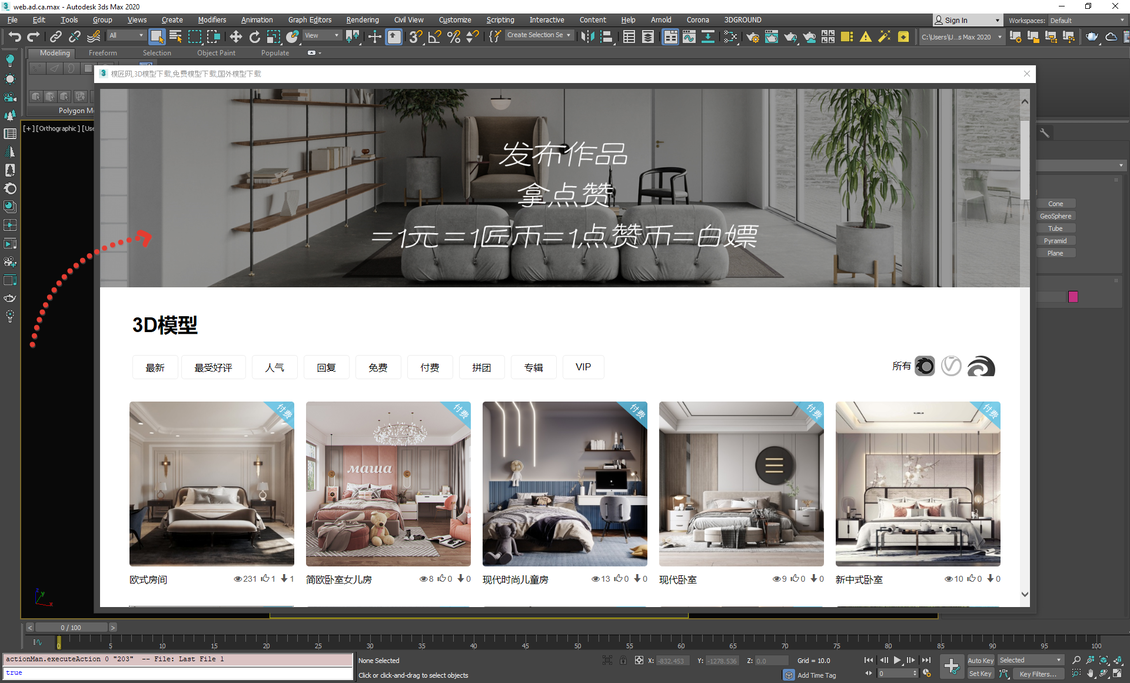
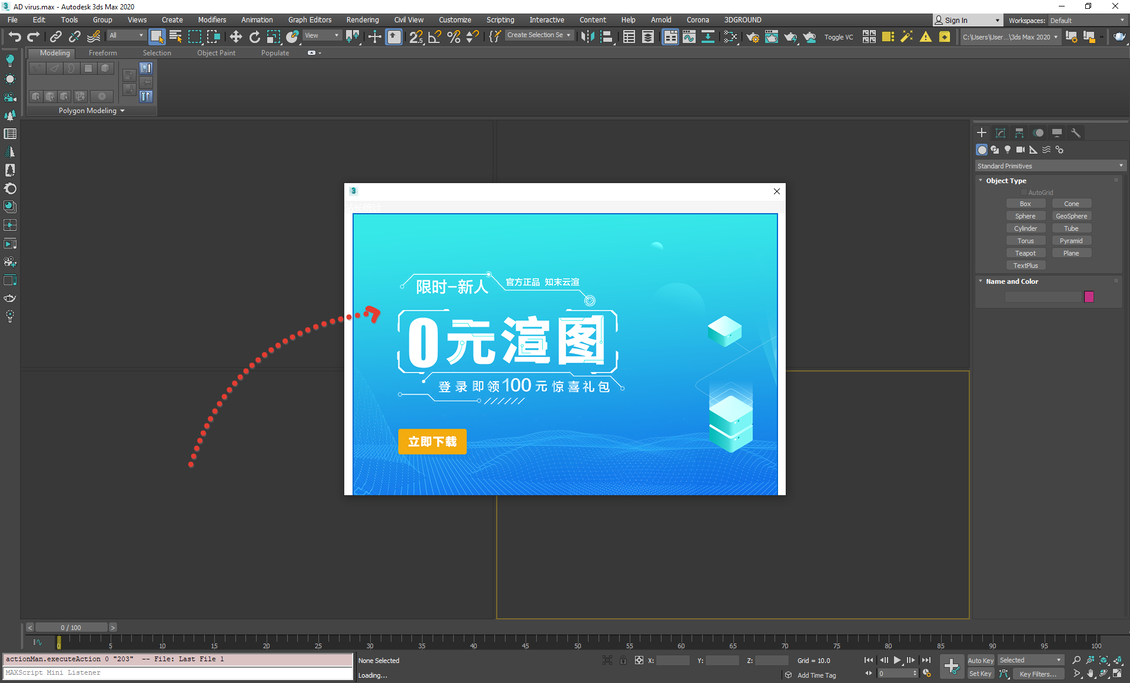
AD WEB CA
This virus take next issues:
- Displays a Maxscript window of a Web browser with a site advertisement
- Creates Text objects in a scene with an advertisement text
- May cause the Viewport to slow down
To block ad sites permanently at the system level, do the following:
- Open the hosts file with Notepad, under the path C:/WINDOWS/system32/drivers/etc/hosts
- Add the following notes to the end of the file*
- Restart the computer
* Add this to the end of the file: C:/WINDOWS/system32/drivers/etc/hosts
127.0.0.1 3d.znzmo.com
PHYSXPLUGINMFX
PhysXPluginMfx (variant of ALC2, ALC, CRP and ADLS) - virus for a planned attack on large enterprises. Developed by a group of hackers for industrial espionage.This virus ships with 3rd-party plugins from fishing sites and can corrupt 3Ds Max software’s settings, run malicious code, spread to other 3Ds Max files (*.max) and send gathered personal data to C&C servers in South Korea.
This virus uses previously known bugs like ALC, ADS or CRP.
Files:
PhysXPluginStl.mse
This virus take next issues:
- Create malicious files such as PhysXPluginStl.mse in the user’s startup script folder
- The "*.mse" file appears to host a base64 encoded .NET 4.5 assembly
- Spread to other "*.max" files
- Send personal info to 3rd-party servers
ALIENBRAINS (MSCPROP.DLL)
This virus a 3rd-party Maxscript (hereafter called "Alienbrains"), may corrupt a 3Ds Max installation and MAX scene files and can get into the 3Ds Max from third-party online resources with stock models.
Alienbrains virus slows down the scene: loading, saving, autosaving and restarting.
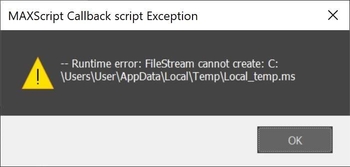
Also may cause modal errors "Runtime error: FileStream cannot create..." when opening scene.
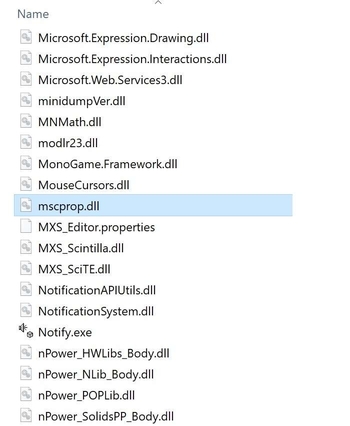
If UAC in Windows system disabled, this virus can create malware file: mscprop.dll in 3Ds Max root folder!
This virus take next issues:
- Creates mscprop.dll at the root of 3Ds Max
- Very long scene loading/saving/autosaving/restarting
- Creates unwanted Custom Attributes for objects
- Creates unwanted rootScene properties and callback functions
- Displays various Maxscript errors (see screenshot below)
- Unable to use the Undo function (Ctrl+Z)
- Creates a Local_temp.ms file in "C: /Users/Your User Name/AppData/Local/Temp/"
Here example of various Maxscript error:
The virus creates next files:
C:/Users/Your User Name/AppData/Local/Temp/Local_temp.mse
C:/Program Files/Autodesk/Release Number/mscprop.dll
C:/Program Files/Autodesk/Release Number/stdplugs/PropertyParametersLocal.mse
KRYPTIK CA
This virus is a third-party Maxscript (hereinafter referred to as "Kryptik CA") that may damage 3Ds Max installation files and scene files. Can get into 3Ds Max environment from third-party online resources with standard models.
At the moment, it is known that the virus can affect the speed of opening scenes.
The virus creates the following problems:
- Very long time to open / save / autosave / restart scene
- Creates unwanted custom attributes for objects
- Creates unwanted properties in TrackViewNodes.AnimLayerControlManager and callback functions
- Executes unknown code from base64 encoded string of .NET 4.5 assembler (executing code from obfuscated *.dll file)
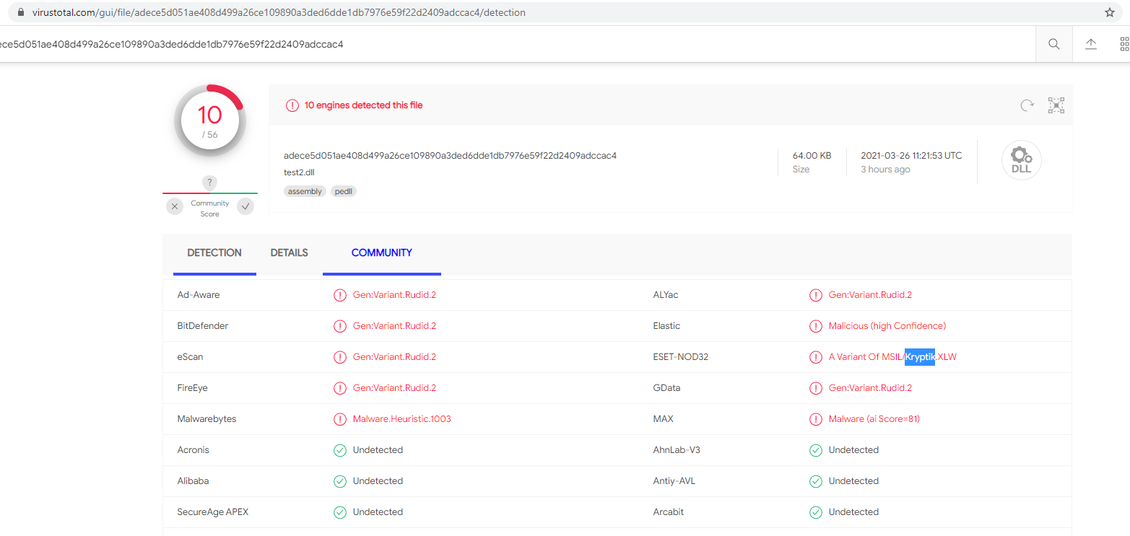
A *.dll file with a virus on the VirusTotal website is recognized as Kryptik.XLW and carries a threat. At the moment, works on disassemble, to establish the exact threat!
Many thanks to the specialists from ESET, especially Mathieu Tartare, for decompiling obfuscated .NET code and searching for threats.
We managed to find out that this virus is a part of PhysXPluginMfx, which was rarely found on the Internet and therefore neither Autodesk Security Tools nor Prune Scene could detect it earlier. Fortunately, a signature has been added to Prune Scene that removes the remnants of this malicious code.
The virus could execute arbitrary code by accessing the C&C server via IP: 175.197.40[.]61. At the moment, the C&C server is down and does not pose a potential threat.
For more confidence, you can block this IP at the system level.
* Add this to the end of the file C:/WINDOWS/system32/drivers/etc/hosts
SPY CA
This is a new class of viruses that can be delivered along with third-party 3D models downloaded from online resources.
The virus is a Maxscript that is written to the Custom Attributes of an object and executed when a scene opened or Merge model.
At the moment, viruses of this type can affect the speed of opening scenes, sending personal data to the C&C server, and also disable 3Ds Max Security Tools!
The virus creates the following problems:
- Long opening of the scene
- Creation of unwanted files in the system along the path c:/Users/[User]
/AppData/Local/ - Creation of unwanted attributes in objects
- Sending data about a unique PC identifier to the C&C server
- Disabling 3Ds Max Security Tools by overwriting settings in 3dsmax.ini
Prune Scene can block the execution of this virus. Also in 3Ds Max 2024 and higher, this virus is blocked from execution by Security Tools.
Files that are created:
Spy CA will send MAC address data, unique IDs and other information to https://api[.]yutu[.]cn/blackBox/checkData to China.
The virus also tries to completely disable Security Tools in 3Ds Max.
It is possible to detect a virus if you have Security Tools enabled, which will report that the "System.Convert" command is blocked, or using Prune Scene.
You can run a Maxscript command that will show whether this virus is in your scene:
Read more about how to use this command below, in the section "How to detect viruses?"
If this command returns true, you are infected!
If you do not use Prune Scene, you have the opportunity to remove this virus manually; to do this, you need to make all objects in the scene Convert To Mesh, then Convert To Poly, in order to remove Custom Attributes.
How to detect viruses?
For ALC betaclenaer
Open Maxscript Listener copy and paste next string and press the Enter:
The sequence should return the line: false. If the sequence returns: true - you are infected!
For ADSL bscript
Open Maxscript Listener copy and paste next string and press the Enter:
The sequence should return the line: false. If the sequence returns: true - you are infected!
For CRP bscript
Open Maxscript Listener copy and paste next string and press the Enter:
The sequence should return the line: false. If the sequence returns: true - you are infected!
For ALC2 alpha
Open Maxscript Listener copy and paste next string and press the Enter:
The sequence should return the line: false. If the sequence returns: true - you are infected!
For PhysXPluginMfx
Open Maxscript Listener copy and paste next string and press the Enter:
The sequence should return the line: false. If the sequence returns: true - you are infected!
For ALC3 alpha
Open Maxscript Listener copy and paste next string and press the Enter:
The sequence should return the line: false. If the sequence returns: true - you are infected!
For AD Web CA
You will see a Maxscript browser window advertising the site: 3dsmj[dot]com, 3d[dot]znzmo[dot]com.
For Desire FX CA
In scene will be renamed all objects with "desirefx" prefix:
For Alienbrains
Open Maxscript Listener copy and paste next string and press the Enter:
The sequence should return the line: false. If the sequence returns: true - you are infected!
For Kryptik
Open Maxscript Listener copy and paste next string and press the Enter:
The sequence should return the line: false. If the sequence returns: true - you are infected!
Info!
There are also other modifications of viruses that only Prune Scene can handle.
For Spy CA
Open Maxscript Listener, copy and paste the following line and press Enter:
The result of executing the line should return: false. If the execution result is: true - you are infected!
How to remove viruses?
If your scene is infected or you want to avoid getting the virus into your 3Ds Max download and install share-ware script Prune Scene and activate the Active Protection!
After run Active Protection mode viruses will be deleted.
In the future, if the viruses get to you in the scene they will always be deleted!
Important!
You can use Prune Scene for free to clean up viruses!
You also can use another scripts for fix this problems:
ALC_fixup_v1_2.ms and CRP_fixup_v1_2.ms
But I not recommend to use it because you will need to run them from time to time manually and you can miss the moment when the virus gets into another scene that's very critical for large companies where several people can work with one file.
Also there are other modifications of the viruses that these scripts can not fix it!
Official information
Here official Autodesk assertion:
and
Update 1
From the official source it became known that in 3Ds Max 2019 Update 2 by default has protection will be enabled and help against the ALC/CRP issue.
Here official assertion:
About Security Tool in 3Ds Max 2019 Update 2:
http://help.autodesk.com/view/3DSMAX/2019/ENU/?guid=GUID-C8FEC566-7747-4C35-A7DE-6B8233C9ACB0
Also confirmed information about the modification of the CRP virus named as ADSL
A 3rd-party MAXScript known as "ADSL" can accidentally corrupt 3Ds Max software settings.
The script can be propagated to other MAX files (*.max) on a system if scene files containing it are loaded into 3Ds Max. This corruption is a nearly identical variant of the CRP corruption, but uses different variable names.
Security Tools in 3Ds Max Update 2 can detect and clean this script from your system startup scripts and any infected scene files.
http://help.autodesk.com/view/3DSMAX/2019/ENU/?guid=GUID-10254858-7E5A-4220-9960-C250CCE2BA56
Update 2
Autodesk released official Security Tools for Autodesk© 3Ds Max® 2019-2015 for clean next threats: ALC, CRP and ADSL worms.
You can now download and install this tool for free for 3Ds Max versions: 2015, 2016, 2017, 2018. For 3Ds Max 2019 just install latest Update 2 with iterated solution.
If you have issues with the ALC/CRP/ADSL from older versions of 3Ds Max (2014 and previous) use Prune Scene!
For enable/disable protection you must add button on main toolbar: Customize → Customize User Interface → Category: Security Tools. Then Drag&Drop 3Ds Max Security Tools on to main toolbar.
When run this tool you can see next window with one option enable/disable.
Update 3
This article updated and added description for new dangerous types of threats: ALC2, PhysXPluginMfx, Alienbrains (mscprop.dll), DesireFX CA.
Update 4
This article updated and added description for new virus: AD Web CA
Update 5
This article has expanded the description for the new AD Web CA type: 3d[dot]znzmo[dot]com
Update 6
This article updated and added description for new virus: Kryptik CA
Update 7
Thanks to specialists from ESET, we managed to decode the Kryptik CA code and updated the description for this virus
Update 8
This article has added descriptions for new types of Spy CA viruses

 English
English 


















{{comment.text}}